In the rapidly evolving digital landscape, browser security has become a paramount concern for users and organizations alike. One of the most insidious threats that has emerged in recent years is the so-called “Universal Browser Virus.” This article delves into the nature of this virus, its impact on users, and the strategies for mitigating its effects.
Understanding the Universal Browser Virus
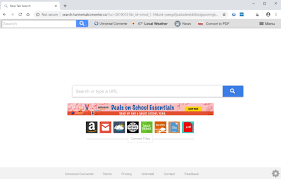
The term “Universal Browser Virus” might sound like a catch-all term, but it refers to a specific type of malware that targets web browsers, exploiting vulnerabilities to compromise user data and system integrity. Unlike traditional viruses that might target a single application or operating system, the Universal Browser Virus is designed to be platform-agnostic, meaning it can affect multiple browsers across various operating systems.
Characteristics of the Universal Browser Virus
- Cross-Browser Compatibility: The Universal Browser Virus is not limited to one browser or operating system. It can affect popular browsers such as Google Chrome, Mozilla Firefox, Safari, and Microsoft Edge. This broad compatibility makes it particularly dangerous, as it can potentially infect a wide range of users.
- Data Theft: One of the primary objectives of this virus is to steal sensitive information. This might include login credentials, financial information, and personal data. The virus often uses techniques like keylogging, form scraping, and session hijacking to gather this data.
- Ad Injection: The virus may also inject unwanted ads into web pages, leading to a degraded user experience. These ads might be benign but often serve as a medium for further malware distribution or phishing attempts.
- Remote Control: Advanced variants of the Universal Browser Virus may allow attackers to gain remote control over the infected browser. This can lead to further exploitation of the system and the potential for other types of malware to be installed.
How the Virus Spreads
The Universal Browser Virus spreads through various vectors, making it difficult to pinpoint a single source of infection. Some common methods of dissemination include:
- Malicious Extensions: Attackers often disguise the virus as a legitimate browser extension. Once installed, the extension can gain access to the user’s browsing activity and sensitive information.
- Phishing Campaigns: Phishing emails or websites can trick users into downloading the virus. These deceptive communications often appear to be from reputable sources, luring users into clicking on malicious links or attachments.
- Exploiting Vulnerabilities: Browsers and their plugins are frequently updated to patch security vulnerabilities. The Universal Browser Virus may exploit unpatched vulnerabilities to gain access to a user’s system.
- Drive-By Downloads: Simply visiting a compromised or malicious website can trigger a download of the virus. These sites often use deceptive tactics to force the download onto the user’s device.
Identifying an Infection
Detecting the Universal Browser Virus can be challenging due to its stealthy nature. However, certain signs may indicate an infection:
- Unusual Browser Behavior: If the browser starts behaving erratically, such as redirecting to unfamiliar sites or displaying unexpected ads, it could be a sign of an infection.
- Slow Performance: A significant slowdown in browser performance might indicate that the virus is consuming system resources or performing background operations.
- Unrecognized Extensions: The appearance of unfamiliar or suspicious browser extensions could be a red flag.
- Data Breach Alerts: Receiving notifications about compromised accounts or suspicious login attempts might suggest that your data has been stolen by the virus.
Mitigation Strategies
Protecting against the Universal Browser Virus requires a multi-faceted approach involving preventive measures, detection, and response strategies.
Preventive Measures
- Update Regularly: Ensure that your browser and any installed plugins are kept up-to-date with the latest security patches.
- Use Reliable Extensions: Only install browser extensions from reputable sources and avoid those that request excessive permissions.
- Enable Security Features: Utilize built-in browser security features, such as pop-up blockers and anti-phishing tools, to reduce the risk of infection.
- Educate Users: Raise awareness about the dangers of phishing emails and malicious downloads. Encourage users to be cautious when clicking on links or downloading files.
Detection Tools
- Antivirus Software: Employ robust antivirus software that can scan for and detect browser-based malware.
- Browser Security Add-Ons: Use additional security add-ons that can help identify and block malicious activities.
- Regular Scans: Perform regular scans of your system to detect and remove any potential threats.
Response Actions
- Isolate the Infection: If an infection is detected, disconnect the affected device from the internet to prevent further data leakage.
- Remove Malicious Extensions: Uninstall any suspicious browser extensions and clear the browser cache.
- Change Passwords: Change passwords for all affected accounts and enable two-factor authentication where possible.
- Seek Professional Help: If the infection is severe or difficult to remove, consider seeking assistance from cybersecurity professionals.
Case Studies and Real-World Examples
Case Study 1: The “Browser Hijacker” Incident
In 2022, a significant outbreak of the Universal Browser Virus led to widespread browser hijacking incidents. Users reported that their browsers were being redirected to phishing sites that mimicked popular banking institutions. The virus was distributed through a malicious browser extension that had been disguised as a productivity tool. Once installed, the extension altered browser settings to redirect users and capture sensitive data.
Case Study 2: The “Ad Injection” Scandal
Another variant of the Universal Browser Virus was discovered injecting unwanted ads into users’ browsing sessions. This variant was distributed via drive-by downloads from compromised websites. The ads not only disrupted the user experience but also included links to further malware. The infection was traced back to a network of malicious ad servers that exploited browser vulnerabilities.
The Future of Browser Security
As the threat landscape continues to evolve, so too must our approach to browser security. The Universal Browser Virus represents a significant challenge, but it also highlights the need for ongoing vigilance and adaptation in our security practices. Future developments in browser technology and cybersecurity measures will play a crucial role in addressing these threats.
- Enhanced Browser Security Features: Future browsers are expected to include more advanced security features, such as improved sandboxing and stricter extension permissions.
- Artificial Intelligence: AI and machine learning may become integral in detecting and mitigating browser-based threats, providing real-time protection against evolving malware.
- User Awareness: Continued efforts to educate users about safe browsing practices will be essential in reducing the impact of such threats.
Browser
The Universal Browser Virus represents a serious threat to online security, exploiting the ubiquity of web browsers to compromise user data and system integrity. Understanding its characteristics, methods of spread, and strategies for mitigation is crucial for protecting against this and similar threats. By staying informed and implementing robust security practices, users and organizations can better safeguard their digital environments against these pervasive and evolving dangers.